Frictionless DevSecOps
Complete SBOM Management Solution
Bytesafe Observer provides a comprehensive SBOM workflow to help you manage your software supply chain. Leverage the powerful combination of the Policy Engine and Operational Model to guarantee the security and compliance of your software.
- Software Composition Analysis
Integrate with your existing CI/CD pipeline and gain insights and control of your software supply chain - throughout the full application lifecycle.
- Policy Compliance
Define and enforce policies for vulnerabilities, deployments, data flow and ownership to ensure your software supply chain is secure and compliant.
- SBOM Workflow
Ingest, Manage, and Share SBOMs across your organization. Analyze and monitor your inventory for vulnerabilities and compliance issues.
Software Bill of Materials (SBOM)
A “software bill of materials” (SBOM) is a nested inventory, a list of ingredients that make up software components such as applications, services, containers and operating systems. SBOMs have emerged as key building blocks in software security and software supply chain risk management.
The “Minimum Elements” defined under Executive Order 14028 are available on the NTIA SBOM Publications page.
An SBOM-related concept is the Vulnerability Exploitability eXchange (VEX). A VEX document is an attestation, a form of a security advisory that indicates whether a product is affected by a known vulnerability.
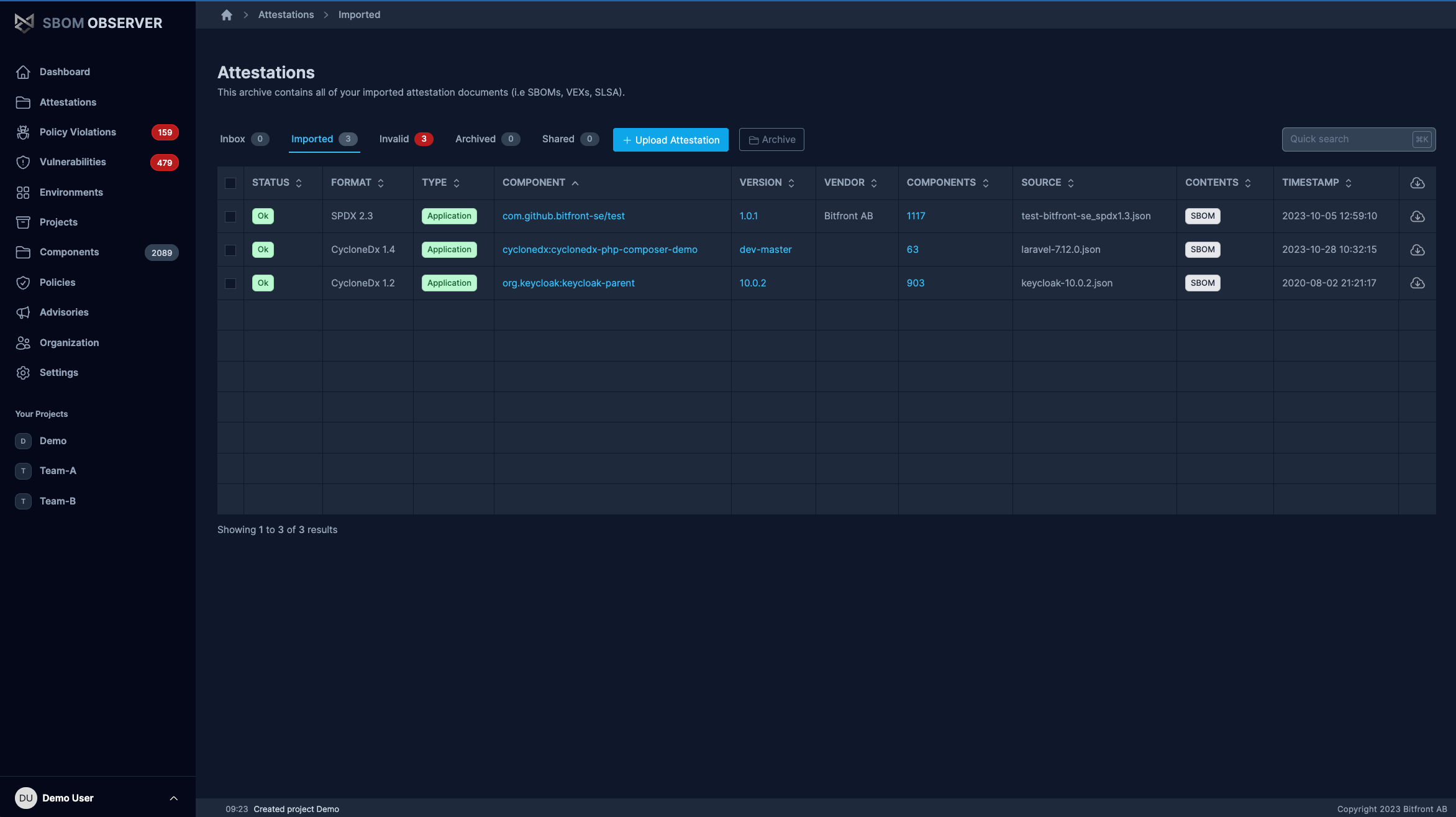
SBOM Management
An Attestation Workflow
Ingest, Enrich, and Share SBOM, SLSA and other attestations types across your organization.
- Attestation Inbox
- Effortlessly receive SBOMs from your suppliers and partners through a variety of channels, including email. With a single, unified inbox, you can efficiently verify and automate these imports.
- Not only SBOMs
- With native support for SLSA attestations, you can monitor and enforce provenance and other claims for your software.
- Share with your customers
- Export and share aggregated SBOMs with your customers and Vulnerability Exploitability eXchange (VEX) and vulnerabilities.
Software Composition Analysis
Open Source Inventory
Automatically identify the open source components in your software and any associated vulnerabilities or risks.
- Integrated with your CI/CD
- Smoothly integrate your CI/CD pipeline and automate the process of generating and importing up-to-date SBOMs for each build and release.
- Open Source Risk Management
- Open Source components make up 85-90% of the codebase in many modern applications and provide a significant threat surface.

Operational Model
Organize Your Inventory
Connect how you actually view services, applications and teams with your inventory of components. Remove noise by prioritizing vulnerabilities and policy violations in applications that are actually running in production.
- Track what is running in production
- Immediately know what environments are impacted by a specific vulnerability.

Vulnerability Management
Continuous Vulnerability Scanning
Your inventory of application, services and containers are continuously scanned for vulnerabilities. Integrations with OVS, GitHub Advisories, NVD and other sources ensure a comprehensive coverage of new vulnerabilities.
- Resolve issues in production first
- Leverage the operational model to prioritize vulnerabilities and policy violations in production environments first.
- Vulnerability Exploitability eXchange (VEX)
- Keep track of exploitability risk assessments for vulnerabilities using VEX documents. Create, import and share CISA VEX compliant documents with your customers and vendors.

Compliance
Automated Policies
SecOps and compliance professionals can leverage the powerful policy engine to monitor and enforce policies throughout the SDLC, including services deployed in production environments.
- Cover the Entire Operational Model
- Policies cover the entire operational model including vulnerability remediation.
- Policy as Code
- The policy engine is integrated with Open Policy Engine (OPA) and SecDevOps engineers can, in addition to our visual policy builder, leverage existing skill sets and implement policies directly in Rego or JavaScript.
- License Compliance
- Automatically track license compliance issues and restrict problematic or unlicensed packages.

Explore SBOM Observer: Let's connect!
Elevate your approach to software bill of materials management with our innovative tool. Connect with us today.
- Complete SBOM Management
- Ingest, Enrich & Share SBOMS
- Support for 25+ ecosystems
- Integrates with your CI/CD
- Uniquely connects Operational models
- Commercially Supported
A Full Stack SBOM Platform
- SBOM Management
- Create, Import, Share and Manage SBOMs throughout the software development lifecycle. Full support for standards such as CycloneDX, SPDX, VEX.
- SLSA Support
- While SBOMs provide you with an inventory, SLSA (Supply-chain Levels for Software Artifacts) enables you to track artifact integrity, that the source code you’re relying on is the code you’re actually using, across your software supply chain.
- Vulnerability Detection
- Detect known vulnerabilities in your inventory of applications, components and containers across wide selection of ecosystems. We integrate many of the standard advisory databases, including GitHub, OSV and NVD.
- Exploitability Analysis (VEX)
- Triage and add vulnerability explotability analysis ('Is this exploitable in this particular application?') to detected vulnerabilities, and share findings with your customers.
- Policy-driven Compliance
- Codify your security and quality policies and enforce them across your entire SDLC with a powerful Policy Engine based on Open Policy Engine (OPA).
- Policy as Code
- In addition to our visual policy builder, DevSecOps professionals can leverage their existing skill set and drop down to Rego or JavaScript when implementing policies.
- Operational Model
- Connect your organizations internal view of teams, services, applications, containers and deployments with the inventory provided by SBOMs and other tools.
- Track Releases
- Track deployments of releases to production environments in the operational model and leverage that information in policies - reducing the noise and helping prioritization of vulnerabilities and violations.
- CI/CD
- Easily integrate your CI/CD pipeline using popular tools and our broad support for SBOM standards and ready made solutions (e.g. GitHub Actions or using our API).
- Automatic Discovery of Applications
- Automatically synchronize your operational model integrations for Kubernetes and AWS ECS, making sure you have an up to date picture of what is running in production. (On the roadmap)
- Exploit Prediction Scoring
- Use the Exploit Prediction Scoring System (EPSS) in combination with the Operational Model and other threat signals to prioritize remediation of detected vulnerabilities.
- CISA VEX
- Create and share CISA compliant Vulnerability Exploitability eXchange (VEX) data to communicate the exploitability of vulnerable components in the context of the product customers or partners are using.
- API Integration
- Use the API for integration with SBOM Observer in your pipelines and to automate workflowsOur API is compatible with the
Pricing
Pricing plans for teams of all sizes
Choose a plan that matches your team size, support and capacity needs.
Professional
The essentials for small teams.
- Full stack SBOM management
- 1 Namespace
- 1 Environment
- 2 Projects
- 2 Business Days Support
- Fully Managed (SaaS)
Business
For DevSecOps and Compliance teams.
- Full stack SBOM management
- 1 Namespace
- 3 Environments
- 10 Projects
- 1 Business Day Support
- Fully Managed (SaaS)
Enterprise
Dedicated support and infrastructure for multiple teams.
- Full stack SBOM management
- Unlimited Namespaces
- Unlimited Environments
- Unlimited Projects
- 100 users included
- SAML integration
- Role Based Access Controls (RBAC)
- Audit Logs
- Service Level Agreement
- Prioritized support with dedicated support channels
- Fully Managed (SaaS) or On-Premise
Frequently Asked Questions
Can’t find the answer you’re looking for? Reach out to our customer support team.
- What is a 'Namespace'?
- Namespaces are isolated data containers for all data managed by Bytesafe Observer, including SBOMs, environments, policies and access controls. Namespaces can be used to separate the data for different organizational units, data for testing purposes etc. Users can have different roles in different namespaces.
- What is an 'Environment'?
- Environments are used to model deployed applications, services, containers and endpoints (VMs, bare metal machines, k8s clusters etc.). Environments are often scoped to production (and testing, QA etc.), but can also be used to model customer deployed systems and more.
- What is a 'Project'?
- Projects are used to group applications, services and components that are related to a specific product or team.
- Is Bytesafe Observer Open Source?
- Currently no. We will reevaluate a possible Open Source version once the product is no longer in beta.
- Do you offer volume discounts?
- Yes, we offer volume discounts to organizations with many users. Let's talk about your requirements and number of users - Contact our customer success team for more information.
- Can we deploy Bytesafe Observer On Premise?
- Yes! Contact our customer success team for more information.
Product Development Roadmap
Upcoming features
SBOM Observer is developed continuously, and we're eager to give you a glimpse into our plans. Our high-level roadmap showcases the milestones we've reached, the new capabilities we're actively working on, and the exciting features we have in mind.
Curious about something or have ideas? Get in touch - we're all ears!
Current release
Provides a full SBOM management suite
- Ingest, enrich and export SBOMs (including VEX)
- Support for both CycloneDX and SPDX standards
- SLSA attestation support for enhanced security
- Compatibility with over 25 ecosystems for extensive vulnerability notification
- Graphical visualization for impact analysis of vulnerabilities
- Advanced Policy engine to reduce the number of vulnerabilities to the ones requiring attention
- Support for Policy as Code using JavaScript or Rego
- Robust data model built for complex application landscapes at scale
Next in Line
Features currently in development
- Sharing SBOMs with stakeholders
- Enhanced multi-namespace support for granular organizational structures
- Extended capabilities for policy management
- Enriched component detail reporting
On the Horizon
Planned initiatives from our development backlog
- Pre-configured Azure DevOps Tasks for simplified CI/CD workflow integration
- Advanced automation features ('if this, then that' logic)
- Signing and verification processes for signed attestations
- Seamless Kubernetes integration with auto-import functionality
